You may have heard about the latest certificate vulnerability, this one from Dell. There are actually two certificates that are exposed, one called eDellRoot which is factory installed by the Dell Foundation Services application, designed to make support easier. The 2nd one is probably less common, it is called the DSDTestProvider certificate, and is only installed by someone that went to Dell’s support site, and ran the Dell System Detect application.
Both of these certificates should be removed. To assist in that, we have created two scripts for Kaseya.
First script (Dell root cert Audit) is an audit script that will scan the machines and record if either of the certificates are present. It writes to the script log with the tag “ *$DellCert$* ” so you can filter it out in a report from Info Manager. If you want to ONLY see the machines that are affected, use the *$OOD$* tag.
The 2nd script (Dell root cert fix), runs Dell’s utility, and also checks for the certificates and then cleans.
** Virtual Administrator Hosted Kaseya and Go!Manage partners can find these under “_VA Scripts, Security”
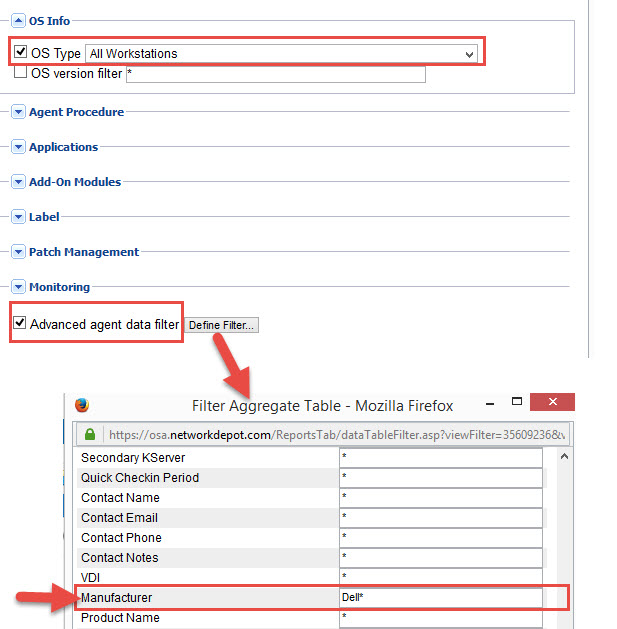
Ideally you should create a view, or use Kaseya’s “zz[SYS] HW – Dell Workstations only” since there is no point in running this on non-Dell machines. If you don’t have the default Dell view, you can create one simply by adding the “Dell*” to the Manufacturer filter under the Advanced Options in the View (see below)
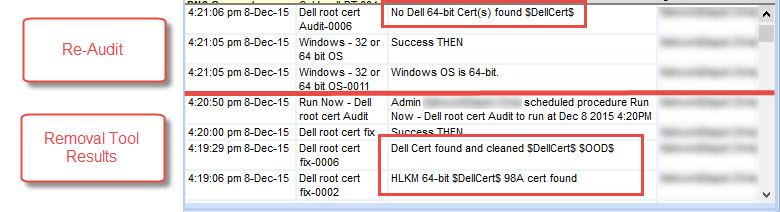
Here is an example procedure log for a machine that had the certificate, had it cleaned, and then re-audited to show it was gone.