The Webroot web console commands for remote scripting — since removed from their product to prevent future intrusions.
In the past month there have been numerous articles about cities and MSPs who have gotten busted with cryptoware. Damages vary from a few hundred thousand to tens of millions in lost time and revenue. As MSPs we are in a sweat-inducing position of not just being responsible for our own machines, but also the health of all our client’s endpoints.
It is bad enough when a client manages to screw their own machines by falling prey to some social engineering scam. But the worst feeling in the world is when you allow a hacker to break into your system and deploy a malicious package to your endpoints. Your clients probably aren’t even aware that your tools such as your RMM, Anti-virus, and backup software can be used as a payload delivery mechanism by malicious hackers. They trust that you have your act together and are hoping that you will help them to remain secure.
Here at Virtual Administrator we have been taking account security very seriously for a long time now. Last year we forced all our Hosted Kaseya partners to begin using AuthAnvil 2FA. There were some complaints, but overall, I think everyone sleeps better knowing that they won’t be that MSP in the news paying $150,000 to unlock their client’s machines.
We have many different services here at Virtual Administrator and wanted to write a little guide on how to enable the security features for each one. Since we are often not in control of development, we can only use the tools that they offer. So check out the sections below to learn more about each of our offerings.
If you have a question about security with any of our platforms, then you can always contact us for more information.
General Security
I think everyone who comes to this post probably already knows most general security measures that an MSP should be taking, but knowing and doing can be two different things so I want to spend a moment to cover the basics. This is as good a time as any to start enacting the basics with account security to ensure that you don’t get hacked.
1.) Use a Password Manager.
Chris uses Lastpass, Kyle and I are both fans of Keepass (I pair this with Dropbox to sync across machines and mobile devices). There are dozens of password managers on the market. It is up to you which one you use but I highly recommend that you use one of them. Password managers mean that you can use highly unique and complex passwords across many different services. No two accounts should have the same password.
You can either use a password generator to come up with long strings of numbers, letters, and special symbols, or you can use words and replace characters with special characters and numbers so they are easier for you to remember. Such as “K@s3y4” (Kaseya).
A password manager can store quite a bit more information than just passwords. You can store notes on your accounts as well as the login links. No more do I have to go through the “do I have an account here?” with websites. Either I do or I don’t.
If you want some ammo for convincing your team and/or your clients to use a password manager. Check out the website haveibeenpwned.com. This site tries to archive how many breaches that emails have been involved in. A casual look showed my personal email address has been involved in 21 breaches including Adobe, Aetna, Home Depot, and a few others. My work email was also involved in several breaches as well. Having unique passwords is vital to securing yourself against these kinds of breaches.
2.) Enable 2FA
Lets face it: 2 Factor Authentication is annoying. But annoying is the price to pay for security. There have been reports of people breaking SMS based 2FA before, but it is rare. Even more rare is people being able to crack 2FA based on an authenticator (such as AuthAnvil, Duo, or Google Authenticator).
If, by some miracle, someone manages to guess your 256 bit password you generated with your password manager then they would need to also have access to your phone in order to generate the 2FA code to finalize the login process.
2FA is vital to the security of your organization. Yes it is bothersome. Yes it can slow things down. Yes you need to keep your phone nearby in order to do your daily work. But how much worse would it be to have to call your client up and tell them that your RMM tool was the reason they lost all of their data?
3.) Train on Social Engineering
Phishing and Social Engineering is pretty much the #1 way people get highjacked these days. Even today in 2019 people still fall for the basic “Hey, open this link” emails. Several security firms offer training programs that you can take and also resell to your clients that train on how to identify these basic threats. This is important for your company, but it is also a solid money-making opportunity to sell it to your clients as well.
4.) Use an Ad Blocker / Script Blocker
Ads can be annoying. But ad highjacking is real. People buy ads on popular services like AdWords and then use those ads in order to build profiles about users around the web. With Chrome killing off proper ad-blocking several of us here are switching over to Firefox for proper adblocking. You can also block things at the Firewall level with services like SonicWall’s content blocking. Or you can setup something like a Pi-hole (or maybe something a bit more robust) which would allow you to block malicious sites from the network.
Keep ads to a minimum and prevent people from digitally fingerprinting you or your clients across the web.
I know most people aren’t malicious in this space. But the few who are are seriously ruining it for everyone else.
5.) Keep Microsoft and Third Party Software Up to Date
Our Ninite script is very useful for keeping third party software up to date. But no matter how you do it, you need to make sure that bugs in software such as Java, Flash, Adobe Reader, and other software isn’t present on your systems or your client systems. Combined with some simple Social Engineering and you might find yourself in some hot water.
6.) Keep MANAGED Backups!
There are a million ways to backup client data. We use Barracuda’s Intronis backup, but I honestly don’t care what you choose to use as long as it meets the follow criteria.
- You can restore client data quickly and effectively.
- Your backup won’t be impacted by crypto-ware.
- Your backup is managed so you can remotely verify it is running successfully and will be notified if it fails.
Take the time to build a real backup strategy and check regularly that it is still running. If something happens to your or your clients it is great if you can simply restore from a backup and move on with life.
Our Product Security Measures
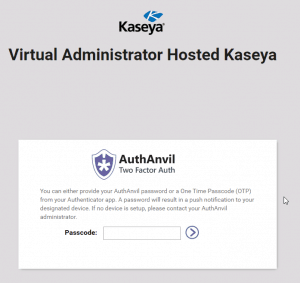
Hosted Kaseya (VA4 and K2)
Our Hosted Kaseya servers) including Go!Manage are protected with AuthAnvil. If you use these servers then you have already been introduced to AuthAnvil. I recommend that you make sure that your account has a unique and strong password. But then AuthAnvil will protect you from that point forward.
Kaseya Saas (Saas2, Saas9, Saas16, and partner.kaseya.net)
If you are on our Saas servers (hosted by Kaseya), then we have good news for you. We have been constantly petitioning Kaseya to enable AuthAnvil for our Saas Clients. Today that dream has become a reality.
If you are on our Saas servers and would like to enable 2FA then please contact us about it and we’ll get you setup ASAP!
Go!Express
Go!Express is our latest iteration of our hosted Kaseya services. This service works a bit different than our previous Hosted Kaseya options. It works more like Kaseya Saas in that your account will operate more-or-less like an independent Kaseya Server.
Because of that we decided not to enforce 2FA. But it is 100% available for this service and we highly encourage it!
Reach out to us to setup 2FA for your Go!Express account.
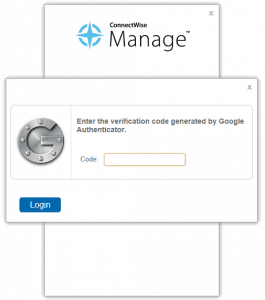
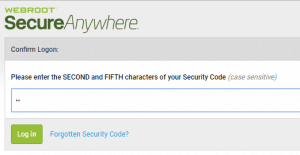
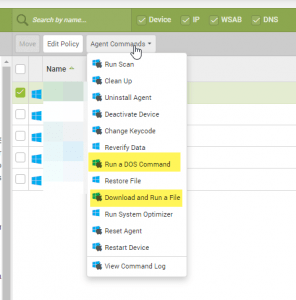
Webroot
Webroot was the recent subject of some public scrutiny because a user at an MSP was highjacked and used to deliver a cryptoware payload. While the fault was not with Webroot, they decided to force enable their “Security Code” feature. This is basically a second password where you enter two random characters in order to help improve the complexity of their login system.
Really, the best security is to use complex and unique logins to their system. The Security code offers some additional security but we are lobbying them to introduce an official 2FA system with their software.
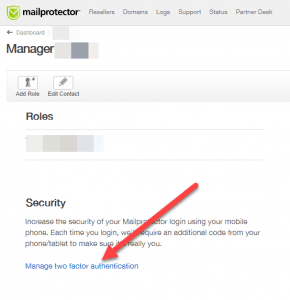
Mailprotector
Mailprotector offers SMS based 2FA. You can find it in your manager settings.
We recommend enabling this setting to protect yourself and your clients.