With yet another Wannacry scare out in the wild it is a good time to take a second and check if your machines are patching properly.
Many of our partners take advantage of our automatic patch policies but they aren’t available across all of our servers and not all of our partners are even using our hosted Kaseya environments. But even if the policy is automatically managed for you that doesn’t mean that there won’t be issues that might stop some machines from patching properly.
The following is a quick 5 step process to check that all is well with your machines and that they are properly patched.
Step 1: Check Patch Policy
Kaseya’s patch policies show patches that are pending install. If the patch isn’t approved in the patch policy then it won’t be installed on any systems associated with that policy. So step 1 is to check for any pending patches, especially for patch policies related to critical and security related patches.
Also make sure all your machines are associated with the default patch policy. Most MSPs won’t need more than one policy, but if you have multiple policies then you will need to ensure that they are all managed on a monthly basis. If you are on our hosted servers (K2 and VA4) then the patch policy is usually managed by us at Virtual Administrator and you won’t have to worry about this step.
Steps 2-5: Patch Status
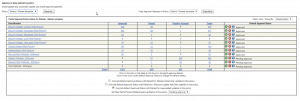
The rest of our checkup process takes place on the Patch Status page. This page shows a per-agent listing of all your agents and any issues that they may be facing. Unfortunately patching machines isn’t always a smooth process, so scanning this page for any issues might quickly bring to light any areas where you may need to focus with individual machines.
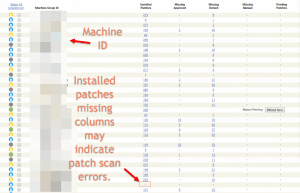
Step 2: Check for scan issues
Fixing scan issues is a bit beyond the scope of this blog post, but machines that have trouble scanning for patches will show a dash in the Installed Patches column.
These machines may have issues with Windows update or may not be setup properly to scan for patches in Kaseya. Try to force a patch scan and you can review any errors from there.
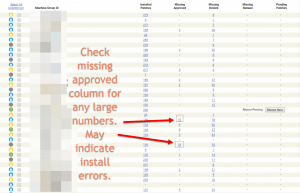
Step 3: Check for “Missing Approved”
There will always be machines with a few missing approved patches. However, if patches are failing to install or the system hasn’t queued up the patch install script properly then you will see a backup of uninstalled approved patches.
The threshold for what constitutes a problem and requires more investigation is a bit debatable. But anything in the double digits will probably be worth inspecting further.
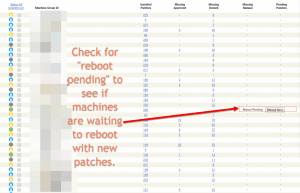
Step 4: Reboot Pending
While this likely isn’t what would qualify as a red flag, checking for “Reboot Pending” shows machines that have new patches installed but have yet to reboot.
Typically servers and other machines that don’t get rebooted or turned off often will need a little extra attention here. Check out our views to view all servers under your management and see if any have “Reboot Pending”.
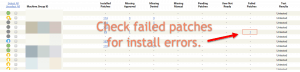
Step 5: Failed Patches
The failed patches column indicates machines that have tried to install patches and have failed for one reason or another. These will require some extra hand-holding. You will want to go into each of these machines and see why the patches are failing to install.
Patches failing to install could cause future patches not to properly install if they are a prerequisite for those future patches (adding to the “Missing Approved” column). So pay attention to this column as it is important to make sure your machines are up to date.
Bonus Step: Check the Microsoft Servicing Stack
Kaseya’s patch management rests on top of the Microsoft Servicing Stack. Historically, Microsoft releases patches for the servicing stack on a twice-yearly basis (or so). However, in recent months Microsoft has been making frequent updates and tweaks to how this system functions so there have been more updates. If the Servicing Stack doesn’t properly patch then it is very possible that your endpoint will show in Kaseya as up-to-date but in reality it could be missing any number of security updates.